Automotive TARA (Threat Analysis and Risk Assessment)
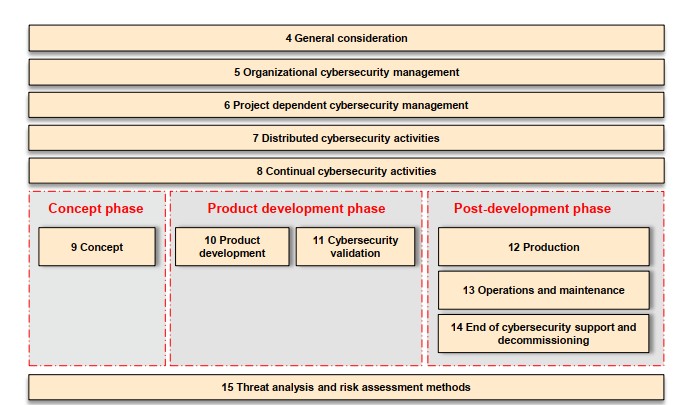
In the automotive domain, cybersecurity is not optional, it’s a mandatory part of ensuring road safety and compliance. Threat Analysis and Risk Assessment (TARA) is a structured approach to identify, analyze, and prioritize cyber threats and vulnerabilities in vehicles' electronic systems. TARA supports the implementation of ISO/SAE 21434 and is crucial in aligning cybersecurity efforts with risk.
RADAR CYBERSECURITYAUTOMOTIVE OTAVEHICLE CYBERSECURITYAUTOMOTIVE ECU CYBERSECURITYECU CYBERSECURITYVEHICLE SECURITYAUTOMOTIVE CYBERSECURITYMICROCONTROLLER CYBERSECURITY SECURITYISO/ SAE 21434AUTOMOTIVE FUNCTIONAL SAFETYAUTOMOTIVE AUTONOMOUS CYBERSECURITYTELEMATIC CYBERSECURITY SOLUTIONS
AutoSec Team
1 min read

TARA helps organizations proactively manage cybersecurity risks by:
- Identifying potential threats to vehicle systems
- Evaluating the risk associated with these threats
- Defining mitigation strategies early in the development lifecycle
- Ensuring compliance with ISO/SAE 21434
- Improving stakeholder confidence and system resilience
While HARA (Hazard Analysis and Risk Assessment) is concerned with functional safety risks due to failures, TARA focuses on risks from malicious attacks. Together, HARA and TARA ensure both safety and security of automotive systems. TARA extends the analysis by incorporating threat sources, attack vectors, and cyber-attack consequences into system evaluation.
The key steps in implementing a comprehensive TARA include:
1. Asset Identification: Define what needs protection (e.g., ECUs, communication buses, backend systems).
2. Threat Scenario Identification: Use STRIDE, HEAVENS, or other models to outline potential attack paths.
3. Impact and Feasibility Evaluation: Analyze the potential damage and likelihood of each threat scenario.
4. Risk Determination: Quantify risk using a predefined risk matrix or scoring model.
5. Risk Treatment Decision: Determine what risks to mitigate, accept, transfer, or avoid.
6. Cybersecurity Goals Definition: Set clear goals aligned with risk levels for system design and controls.
Case Study: Connected Infotainment System
In a connected infotainment module, TARA is applied to evaluate threats such as unauthorized app installation or Bluetooth attack vectors. Assets include the firmware, communication interfaces, and connected services. A STRIDE-based analysis reveals risks of spoofing and tampering. The expected outputs include mitigations such as secure boot, application whitelisting, and Bluetooth authentication protocols.
Risk scoring ranks threats based on feasibility and impact, helping prioritize controls. Cybersecurity goals are defined such as ensuring software integrity and user authentication, contributing to the vehicle’s overall cyber posture.
The expected output of a TARA process includes:
- Documented threat scenarios with impact analysis
- Risk ratings and treatment plans
- Defined cybersecurity goals
- Inputs to the cybersecurity concept and design validation
This documentation supports development traceability and compliance audits.
AutoSec Innovation
Driving Innovation, Securing Tomorrow
Quick Links
Contact Us
info@Autosecinnovation.com
+91-7207205928
© 2025. All rights reserved by AutoSec Innovation Private Limited
#Devparwa, Balliparwa Mirzapur Uttar Pradesh 231001
#Koburger Strass Köln Germany
+49-15171229848
